The process is not over-complicated but deserves to be properly documented.
While IP Cameras claim to be security devices, most of them are completely insecure when it comes to access them: their clear text login is easy to intercept. Only high-end models support SSL encryption,
This is the reason I recently invested into 5 additional Synology camera licenses (CLP4 + CLP1, which means an extra 200€ in total!!
The Smartphone app DS Cam from Synology is far from perfect and only supports MJPEG cameras under a unique multi-view.
HitMob's IP Camera Viewer supports Synology but does not give much information on how to make this work.
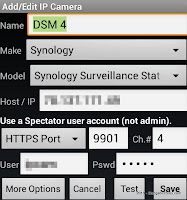
 The very first requirement, at least since DSM 4.x, is to have a non-admin user with nothing else than the Surveillance Station permission.
The very first requirement, at least since DSM 4.x, is to have a non-admin user with nothing else than the Surveillance Station permission.If the user presented by IP Camera Viewer has any sort of administrator privilege, it will be rejected by the NAS.
The next thing is to confirm an HTTPS port for the Surveillance Station via the Syno's Application Portal (here 9901) and to ensure that the router will forward external requests to that port (9901) to the NAS internal IP address.
 |
| click for bigger view |

From there it is just a matter of creating cameras in IP Camera Viewer, using Synology as Make and Synology Surveillance Station as Model, with the right DDNS address, HTTPS port, and login. You must create one entry per camera. Each camera is identified by the field Ch.#
To speed things up, the first camera can be cloned via the application menu and the channel field (Ch.#) will be automatically incremented for each new clone.

Gaining in security requires a trade with functionalities, and you may loose the PTZ control and Audio. At least that's my case with Foscam FI8918W, Tenvis JPT3815W, Tenvis IPRobot3 and Dericam H502W.
See also: Security and IP Cameras